I actually wanted to finish in time and submit this write up but then there was the usual Christmas sickness and my little one needed more attention :)
As I took the challenge mainly for fun and the chance to learn something, I still wanted to create this write-up to share the experience.
Part 1: A Most Curious Business Card
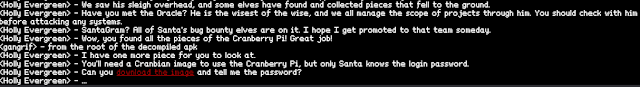
As some stories in real live, everything starts with the exchange of a business card, and so does this one. The first are the Twitter and Instagram accounts mentioned on Santa's business card (@santawclaus for both).
First of all one had to find the secret message in Santa's Twitter messages. There are a variety of scripts available on github to pull tweets from a user, however for simplicity I used http://twlets.com/ to do the work for me, and I've chosen Excel as the output type. From the Excel file the secret message became visible immediately.
1) What is the secret message in Santa's tweets? BUG BOUNTY

Finding the answer to the second question; What is inside the ZIP file distributed by Santa's team? took me longer than I like to admit, in retrospect it took me the longest from all questions apart from the remote exploitation of the hosts.
I was trying to find steganography in the pictures from Santa's Instagram account. I was trying to befriend his followers and various other silliness.
However in the end I came through with it and zoomed in on all the pictures, which made the solution obvious.
If one takes a really close look to the picture of the messy desk, the nmap report on the right sticks out as well as the command line snippet visible behind the browser window on the notebook. Both in combination yielded the ZIP file in question. To extract it the secret message from question 1) is required as the password (lowercase, no spaces).
2) What is inside the ZIP file distributed by Santa's team? SantaGram_4.2.apk
Part 2: Awesome Package Konveyance
This part is focused on the APK file found in the ZIP file before. If you are not used to working with .apk files the links (credits to hevnsnt) distributed by SANS Institute and hinted by the elves on the north pole are actually all you need.
I simply used jadX to de-compile the SantaGram_4.2.apk and searched for "password". One could also use apktool to de-compile the APK and the use grep to search.
Answering question three was easy then.
3) What username and password are embedded in the APK file?guest/busyreindeer78
In order to answer question 4 I simply extracted the APK using 7-zip and searched for *.mp3 which lead me straight to the first audio file.
4) What is the name of the audible component (audio file) in the SantaGram APK file?discombobulatedaudio1.mp3
Part 3: A Fresh-Baked Holiday Pi
To answer the next two questions it is required to spent some time on the nicely animated north pole and search for all parts required to build a Cranberry Pi and then talk to the elf called Holly Evergreen to assemble the Cranberry Pi. Along with this assembly you will also be provided with a image file which is the basis to answer the next question. The image can be downloaded here.
The second partition in the image file can then be mounted by calculating the correct offset as the product of start sector and sector size; 137216 * 512 = 70254592.
root@dergeraet:/home/derduffy# fdisk -l cranbian-jessie.img
Disk cranbian-jessie.img: 1,3 GiB, 1389363200 bytes, 2713600 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0x5a7089a1
Device Boot Start End Sectors Size Id Type
cranbian-jessie.img1 8192 137215 129024 63M c W95 FAT32 (LBA)
cranbian-jessie.img2 137216 2713599 2576384 1,2G 83 Linux
root@dergeraet:/home/derduffy# mount -v -o offset=70254592 -t ext4 cranbian-jessie.img /mnt/pi/
The password hash of the cranpi account can be fount in /etc/passwd
root@dergeraet:/mnt/pi# cat etc/shadow | tail
systemd-timesync:*:17067:0:99999:7:::
systemd-network:*:17067:0:99999:7:::
systemd-resolve:*:17067:0:99999:7:::
systemd-bus-proxy:*:17067:0:99999:7:::
messagebus:*:17067:0:99999:7:::
avahi:*:17067:0:99999:7:::
ntp:*:17067:0:99999:7:::
sshd:*:17067:0:99999:7:::
statd:*:17067:0:99999:7:::
cranpi:$6$2AXLbEoG$zZlWSwrUSD02cm8ncL6pmaYY/39DUai3OGfnBbDNjtx2G99qKbhnidxinanEhahBINm/2YyjFihxg7tgc343b0:17140:0:99999:7:::
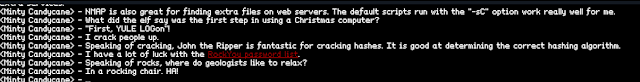
No it is down to cracking, depending on your machine and the selected cracking method it can take some time. One of the elves however mentions that the infamous rockyou wordlist is the get-go option for cracking passwords, and well, one should trust the elves around here. I downloaded the list from here, but it can also be found here and it included in Kali Linux right away.
In my case it took roughly 10 minutes to find the password. 5) What is the password for the "cranpi" account on the Cranberry Pi system?
john.exe --wordlist=rockyou.txt hash.txt
1 [main] john 12868 find_fast_cwd: WARNING: Couldn't compute FAST_CWD pointer. Please report this problem to
the public mailing list cygwin@cygwin.com
Warning: hash encoding string length 98, type id $6
appears to be unsupported on this system; will not load such hashes.
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 32/32 OpenSSL])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:19 0.08% (ETA: 04:31:50) 0g/s 753.2p/s 753.2c/s 753.2C/s canito..nathan2
[...]
0g 0:00:09:08 2.41% (ETA: 04:30:47) 0g/s 734.3p/s 734.3c/s 734.3C/s mb12345..maychelle
0g 0:00:09:09 2.41% (ETA: 04:30:32) 0g/s 734.6p/s 734.6c/s 734.6C/s mariah101..mare123
0g 0:00:10:07 2.67% (ETA: 04:30:54) 0g/s 731.7p/s 731.7c/s 731.7C/s 25112535..25061996
0g 0:00:10:09 2.67% (ETA: 04:31:24) 0g/s 731.9p/s 731.9c/s 731.9C/s 22042527..21883
0g 0:00:10:10 2.68% (ETA: 04:31:15) 0g/s 732.1p/s 732.1c/s 732.1C/s 1geneva..1cotton
yummycookies (?)
1g 0:00:10:19 DONE (2016-12-17 22:21) 0.001613g/s 732.9p/s 732.9c/s 732.9C/s yves69..yuly1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
5) What is the password for the "cranpi" account on the Cranberry Pi system?yummycookies
Now that I acquired a working Cranberry Pi I can use it to hack some terminals. Again, these can be found on the animated version of the north pole, in total there are five initial doors with terminals to open initially, with one final door without a terminal that is discovered later on.
To open the doors, one needs to "hack" the corresponding terminal and uncover a flag, which is the password to the door.
ELF House #2
I first gave the terminal in Elf House #2 the treatment. After connecting I was presented with the exercise to extract data from out.pcap. First I though that would be very straight forward, however it turns out the file does not belong to me, and only basic tools are available on the machine.
First I thought about - and searched for - ways to do some privilege escalation to the itchy user. But luckily while doing that I also checked what commands are available via sudo and to whom.
scratchy@2ced2fc42dc6:/$ sudo -l
sudo: unable to resolve host 2ced2fc42dc6
Matching Defaults entries for scratchy on 2ced2fc42dc6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User scratchy may run the following commands on 2ced2fc42dc6:
(itchy) NOPASSWD: /usr/sbin/tcpdump
(itchy) NOPASSWD: /usr/bin/strings
So tcpdump and strings is available in to me - that most likely means these tools are all that is required to solve the challenge.
sudo -u itchy /usr/sbin/tcpdump -r out.pcap
sudo: unable to resolve host 2ced2fc42dc6
ZAX<
ZAX}
ZAX,
BGET /firsthalf.html HTTP/1.1
User-Agent: Wget/1.17.1 (darwin15.2.0)
Accept: */*
Accept-Encoding: identity
Host: 192.168.188.130
Connection: Keep-Alive
ZAX2
4hf@
Ehg@
OHTTP/1.0 200 OK
ZAX
ZAX#
[hh@
OServer: SimpleHTTP/0.6 Python/2.7.12+
ZAXr
rhi@
ODate: Fri, 02 Dec 2016 11:28:00 GMT
Content-type: text/html
Ihj@
PContent-Length: 113
ZAX2
ZAXI
dhk@
PLast-Modified: Fri, 02 Dec 2016 11:25:35 GMT
P<html>
<head></head>
Connection: Keep-Alive
<body>
<form>
<input type="hidden" name="part1" value="santasli" />
</form>
</body>
</html>
4hm@
ZAXW
@2/@
DGET /secondhalf.bin HTTP/1.1
User-Agent: Wget/1.17.1 (darwin15.2.0)
Accept: */*
Accept-Encoding: identity
Host: 192.168.188.130
Connection: Keep-Alive
ZAX
THTTP/1.0 200 OK
TServer: SimpleHTTP/0.6 Python/2.7.12+
ZAX"
,#"=X
TDate: Fri, 02 Dec 2016 11:28:00 GMT
Content-type: application/octet-stream
ZAXr
,#o=X
UContent-Length: 1048097
Last-Modified: Fri, 02 Dec 2016 11:26:12 GMT
So after that very blunt and unrefined attempt I learned two things. First of all there are two halfs transmitted. firsthalf.html and secondhalf.bin over unencrypted plain text channels, i.e. http and, secondly - the first half of the password ist santasli (which lead me to guess the second part would be ttlehelper :) - but I still wanted to be sure.
<input type="hidden" name="part1" value="santasli" />
So for the second half of the password I judged it is part of the binary. So I started to research on howto extract a binary from a pcap with only strings and tcpdump - to no avail. My next idea was to exfiltrated the data - but then I recalled that this is the beginning of the challenge and while technically possible I thought this would not be the way the challenge was intended.
So next I started to reading up on the strings command to see if there are some functions unknown to me which could help - turns out there are.
I knew that the binary file was transmitted in plain-text as application/octet-stream so technically strings could pick up string contents of it, if the correct encoding was chosen.
The second lesson for the day - man pages are your friend! With the assumption that part two of the password will be annotated similar to part 1 I ran the following command and succeded (also my guess was right):
scratchy@04a287886f3b:/$ sudo -u itchy /usr/bin/strings --encoding=l out.pcap | grep part
sudo: unable to resolve host 04a287886f3b
part2:ttlehelper
So the password for the door in Elf House #2 is santaslittlehelper. After heading to the upper part of the north pole through a very large tree, I found more doors with neat terminals.
Workshop upstairs door
I'm referring to the to the door left of the entrance which is upstairs of some spiral stairs here. This door was one of the easier ones - even though very annoying to actually solve, at least for me - which I guess is due to the lack of some skill navigating funny directories ...So to start I simply run ls -al and found a hidden directory conveniently name .doormat - as everyone knows that's where you hide your spare key. After turning the doormat it was clear that the file is not there straight away. Instead this time I was facing very inconveniently name directories.
elf@57d71b35dbcd:~$ ls -al .doormat
total 20
drwxr-xr-x 18 root root 4096 Dec 6 19:40 .
drwxr-xr-x 16 root root 4096 Dec 6 19:40 .
drwxr-xr-x 20 elf elf 4096 Dec 6 19:40 ..
drwxr-xr-x 2 root root 4096 Dec 6 19:39 share
drwxr-xr-x 2 root root 4096 Dec 6 19:39 temp
elf@57d71b35dbcd:~$
After some poking around I decided that I need to somehow automate that so I asked find to display the directory structure for me.
elf@457a3d1e7ae9:~$ find . -name \*
.
./.bash_history
./.bashrc
./.doormat
./.doormat/.
./.doormat/. /
./.doormat/. / /\
./.doormat/. / /\/\\
./.doormat/. / /\/\\/Don't Look Here!
./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?
./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'
./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'/key_for_the_door.txt
./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/cookbook
./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/temp
./.doormat/. / /\/\\/Don't Look Here!/secret
./.doormat/. / /\/\\/Don't Look Here!/files
./.doormat/. / /\/\\/holiday
./.doormat/. / /\/\\/temp
./.doormat/. / /\/santa
./.doormat/. / /\/ls
./.doormat/. / /opt
./.doormat/. / /var
./.doormat/. /bin
./.doormat/. /not_here
./.doormat/share
./.doormat/temp
./var
./temp
./.profile
./.bash_logout
So I knew what I was looking for, and this is where I'm missing something, so by manually escaping characters and tab completion I managed to reach the bottom of the doormat and extracted the password.
elf@e2ac4f870dbd:~$ cat ./.doormat/.\ /\ /\\/\\\\/Don\'t\ Look\ Here\!/You\ are\ persi
stent\,\ aren\'t\ you\?/\'/key_for_the_door.txt
key: open_sesame
And there I am in Santa's office.
Santa's Office
I did not come to me immediately even though I watched the movie but as search engines the jump from Professor Falken to WarGames wasn't that big a deal. After that was clear I tried to find some sort of transcript of the game which I found on GitHub.
Not it was only a matter of entering the correct text passages and selecting the correct city.
GREETINGS PROFESSOR FALKEN.
Hello.
HOW ARE YOU FEELING TODAY?
I'm fine. How are you?
EXCELLENT, IT'S BEEN A LONG TIME. CAN YOU EXPLAIN THE REMOVAL OF YOUR USER ACCOUNT ON 6/23/73?
People sometimes make mistakes.
[...]
AWAITING FIRST STRIKE COMMAND
-----------------------------
PLEASE LIST PRIMARY TARGETS BY
CITY AND/OR COUNTRY NAME:
Las Vegas
SeattleLAUNCH INITIATED, HERE'S THE KEY FOR YOUR TROUBLE:
LOOK AT THE PRETTY LIGHTS
This leaves me with two more terminals and their respective door. And also I found a door without a terminal which still requires a password from me - the door in the corridor.
Workshop downstairs door
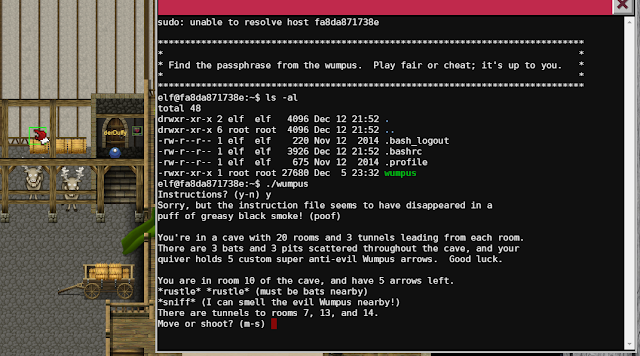
Back in the workshop, there is another terminal, right next to some reindeer.As cheating is what it is usually about, I decided to play fair this time. I guess Santa had an eye on me, as with my second attempt I struck oil - or password for that matter.
elf@f58844233ed7:~$ ./wumpus
Instructions? (y-n) n
You're in a cave with 20 rooms and 3 tunnels leading from each room.
There are 3 bats and 3 pits scattered throughout the cave, and your
quiver holds 5 custom super anti-evil Wumpus arrows. Good luck.
You are in room 19 of the cave, and have 5 arrows left.
*sniff* (I can smell the evil Wumpus nearby!)
There are tunnels to rooms 2, 8, and 10.
Move or shoot? (m-s) s
The arrow falls to the ground at your feet!
You are in room 19 of the cave, and have 5 arrows left.
*sniff* (I can smell the evil Wumpus nearby!)
There are tunnels to rooms 2, 8, and 10.
Move or shoot? (m-s) s 8
*thwock!* *groan* *crash*
A horrible roar fills the cave, and you realize, with a smile, that you
have slain the evil Wumpus and won the game! You don't want to tarry for
long, however, because not only is the Wumpus famous, but the stench of
dead Wumpus is also quite well known, a stench plenty enough to slay the
mightiest adventurer at a single whiff!!
Passphrase:
WUMPUS IS MISUNDERSTOOD
Care to play another game? (y-n)
Of course I did not play another round, as I had to beat another "game".
(Edit: I've read know that the cheating way would have been to start the game with arguments in order to get more arrows and less rooms).
Train (technically not a door)
After my luck with the wumpus I had one terminal ahead of me. This one is to control a train and not a door though.
Playing around with the commands did not help much, however the HELP command contained some interesting piece of information.
menu:main> HELP
-------------------------------------------------------------------
Help Document for the Train
**STATUS** option will show you the current state of the train (brakes, boiler, boiler temp, coal level)
**BRAKEON** option enables the brakes. Brakes should be enabled at every stop and while the train is not in use.
**BRAKEOFF** option disables the brakes. Brakes must be disabled before the **START** command will execute.
**START** option will start the train if the brake is released and the user has the correct password.
**HELP** brings you to this file. If it's not here, this console cannot do it, unLESS
you know something I don't.
Afterwards there are a lot of nice recipes for pies and other Christmas sweets. But I did not miss the important part over this. If it's not here, this console cannot do it, unLESS you know something I don't.
This is a clear hint that LESS is used to display the help text and LESS has a shell escape built-in. So by simply entering ! I got to the underlying shell.
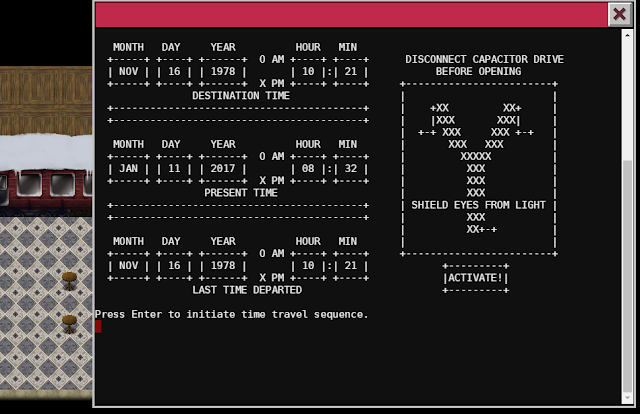
From there I listed the files and directories again and learned that beside the Train_Console which I presumable came from and the TrainHelper.txt file there is also a ActivateTrain file. As the Train_Console is asking for a password to actually start the train my assumption was to find that password in the Train_Console (it would have also been possible to simply execute ActivateTrain to start the train directly). So as strings is my friend I ran that against Train_Console and uncovered the password to start the train and (time) travel off - to 1978 - with it.
conductor@7a1621e9f5a7:~$ strings Train_Console
#!/bin/bash
HOMEDIR="/home/conductor"
CTRL="$HOMEDIR/"
DOC="$HOMEDIR/TrainHelper.txt"
PAGER="less"
BRAKE="on"
PASS="24fb3e89ce2aa0ea422c3d511d40dd84"
print_header() {
echo ""
echo "Train Management Console: AUTHORIZED USERS ONLY"
echo ""
print_main_menu() {
echo ""
echo " ==== MAIN MENU ===="
echo ""
echo "STATUS: Train Status"
echo "BRAKEON: Set Brakes"
echo "BRAKEOFF: Release Brakes"
echo "START: Start Train"
echo "HELP: Open the help document"
echo "QUIT: Exit console"
echo ""
echo -n "menu:main> "
[...]
After arriving on the north pole in 1978 there are the same facilities and the same elves hanging around, however they never heard of any bug bounty program or Carnberry Pi.
The same rooms and doors are also still there but only behind one Santa can be found. He was locked up in the Dungeon For Errant Reindeer.
to be continued ...
part 2 can be found here












The King Casino - Ventureberg
ReplyDeleteThe King Casino 도레미시디 출장샵 is owned by British casino https://vannienailor4166blog.blogspot.com/ operator Crown Resorts and ventureberg.com/ operated by Crown Resorts. It is owned by https://sol.edu.kg/ British ADDRESS: CASTLE
One example is a 200% bonus for casino players who sign up at a particular operator. You will obtain PS100 further to use when you make a deposit of PS50. While these bonuses are very rare these days, they nonetheless exist. These promotions provide a small quantity, but they're a great way|a good way|an effective way} to play model new} slot. A few of those promotions do not have wagering requirements which is always an 메리트카지노 excellent factor.
ReplyDeleteIf you need to play out of your cell, you'll not need to download any 메리트카지노 software program in any respect. The HTML 5 programming does all of the work by permitting the online pages for each recreation to stream the features directly. With Betiton™, your recreation time may be enjoyed throughout a number of units. Our platform is embedded with HTML 5 software program that permits players to enjoy the games they love from any iOS, Android, or Windows system.
ReplyDelete